Vault7: CIA Hacking Tools Revealed

Navigation: » Latest version
Owner: User #14587667
JQJSTEPCHILD - Op2
IP Addresses
2911
gi0/0: 192.168.80.6/30 (TOR5 1/0/13)
gi0/1: XXX.XXX.XX.XXX (HFZ[CN])/28 (TOR5 1/0/3)
TRCore
vlan 501: XXX.XXX.XX.XXX (HFZ[CN])/28
vlan 502: 192.168.80.5/30
Setup: gi0/1 was connected to the TOR switch. gi0/0 (192.168.80.6 was not connected).
Result:
I attempted to ping from the TR Core swx (10.9.8.1) to XX.XXX.XX.XXX (DNIC-SNET-022[US]) and it did not respond. I also tried to ping from a Windows VMVirtual Machine (10.9.8.97) to the 2911 and got no response.
Once I added a route on the 2911 (ip route 10.9.8.0 255.255.255.0 XXX.XXX.XX.XXX (HFZ[CN])) the traceroute returned a result and I was able to ping it from another subnet.
Performing a tracert from a Windows VMVirtual Machine (10.9.8.97), yielded the following results: 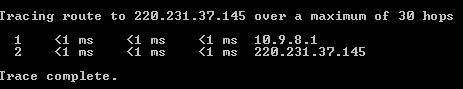
Performing a traceroute from the 2911 to the Windows VMVirtual Machine (with the route still added) yielded the following: 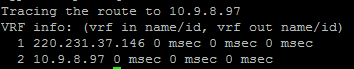
Setup: Both gi0/0 and gi0/1 were connected to the CoreSwx.
Result:
I could ping from the 2911 to 10.9.8.97 (Windows VMVirtual Machine). I could also ping from the Windows VMVirtual Machine to the 2911.
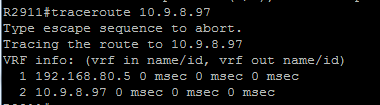
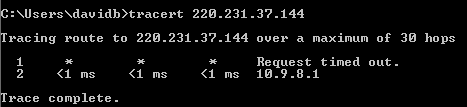
Notes:
6/29/2015
- If I remove the 192.168.80.6 interface from the CoreSwx, then I can no long access the 2911.
- If I remove the XXX.XXX.XX.XXX (HFZ[CN]) interface from vlan501 on the CoreSwx, then I can still access the 2911. I placed a route on the CoreSwx (ip route XXX.XXX.XX.XXX (HFZ[CN]) 255.255.255.240 192.168.80.6).
ToDo
| ID | Status | Task |
|---|---|---|
| 1 | complete | Configure NAT |
| 2 | incomplete | Configure pptp |
| 3 | incomplete | Verify route taken by vpn traffic |