Vault7: CIA Hacking Tools Revealed

Navigation: » Directory » Embedded Development Branch (EDB) » EDB Home » Projects » HarpyEagle
Owner: User #11628962
Test Infrastructure
HarpyEagle is currently focused on investigating the Apple AirPort Extreme and AirPort Time Capsule routers for avenues of access to the filesystem.
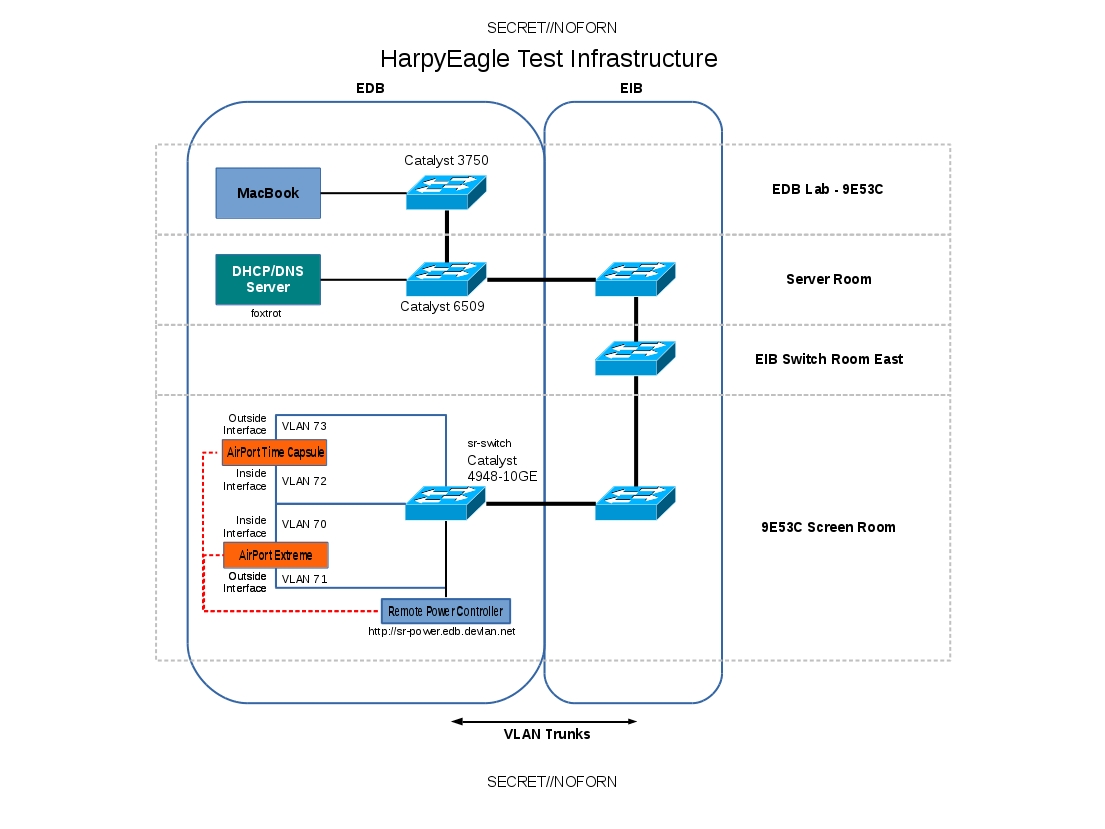
Note: When a device is being tested in bridged mode, the LAN-side switch port (17/19) must be shut or the cable disconnected from the switch. Otherwise, two VLANs will be connected together and error messages on the switch will result.
Port Analysis
External Network Communications Analysis
A DHCPDynamic Host Configuration Protocol and DNSDomain Name System server were connected to the WANWide Area Network port of the device and, over the course of testing, the device performed DNSDomain Name System look-ups for the following URLs:
|
1-courier.push.apple.com
|
|---|
| Initialization Sequence (incomplete) | ||
| URL | Description and/or Assumptions | |
|---|---|---|
| 1 | apsu.apple.com/versions.xml | Get version information |
| 2 | apsu.apple.com/versions.xml.signature | Get version information signature |
| 3 | phobos.apple.com/bag.xml?ix=5 | Resolves to "ax.init.itunes/WebObjects/MZinit.woa/wa/initiateSession?ix=5" |
| 4 | www.apple.com/root.crl | Get root certificate revocation list |
| 5 | crl.apple.com/codesigning.crl | Get code signing certificate revocation list |
| 6 | init.ess.apple.com/WebObjects/VCInit.woa/wa/getBag?ix=1 | unknown |