Vault7: CIA Hacking Tools Revealed

Navigation: » Latest version
Munge Payload
SECRET//NOFORN
Munge Payload
Description:
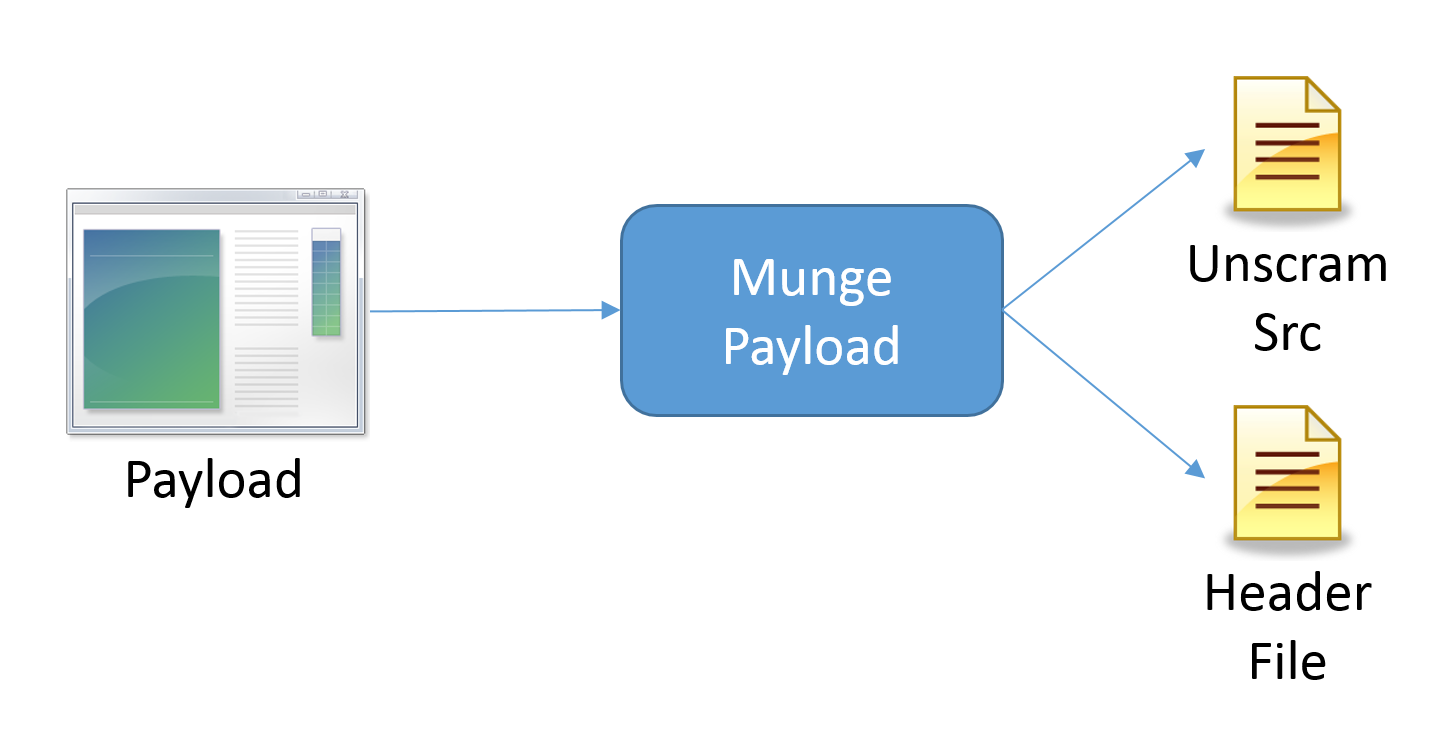
The Munge Payload utility is designed to help automate some of the steps in obfuscating or encrypting embedded payloads.Specifically, Munge Payload is currently capable of supporting the Melomy style of embedding/trojaning. The utility will read in a payload, modify it (or won't) with the specified parameters, and generate a formatted header file with an array containing the payload. The currently supported modifications to the payload are: None, XOR Rolling XOR (RXOR), Compression (ZLIB), AESAdvanced Encryption Standard Encryption, Public/Private Key Encryption, or a combination of these. Currently, the utility will overwrite the header file you specify if it already exists. The tool also generates the deobfuscation/decryption code needed to repair the payload during execution. The order of manipulation if all options are specified is: Compression, XOR, Rolling XOR, AESAdvanced Encryption Standard Encrypt (MSFT_AES_256), Public/Private Encrypt (MSFT_RSA_4096). If you wish to randomize the keys being used (for XOR , RXOR, AES, and Public/Private), you can replace the following argument with the keyword 'gen'. For example, if I want a random key for my XOR, I simply change -x 23 to -x gen.
AES Key FIle Generation: Create a text file -> Open in WinHex -> Resize to 32 bytes -> Edit -> Fill FIle -> Cryptographically secure data
**Note**: When using the gen keyword, the created key is stored in the current directory with the name MungePayloadAESKey.key
RSA (Pub/Priv) Key File Generation: Use KeyGenerator.exe (see repository MungePayload folder) -> Generates privateKey.pem and publicKey.pem
**Note**: When using the gen keyword, the created key pair is stored in the current directory with the file names MungePayloadPubKey.pem and MungePayloadPrivKey.pem.
Files generated by Munge Payload:
- MungePayloadUnscram.txt - Dropped in current directory. Contains unscramble source to de-obfuscate the payload.
- Payload.munge - The obfuscated copy of the payload is dropped in the current directory.
- Header file - Replaced in place or creates in at the location specified.
- MungePayloadAESKey.key - Generated when the gen keyword is used to produce a random AESAdvanced Encryption Standard key.
- MungePayloadPubKey.pem and MungePayloadPrivKey.pem - Generated when the gen keyword is used for Public\Private key encryption.
Random Generation:
- XOR: Uses srand() and rand() to generate a random byte between 5-255. This bytes is used as the key for the XOR. Note, the unscram will not change when using the gen keyword (user-supplied key will cause the source to change when the supplied key changes).
- RXOR: Uses srand() and rand() to generate a random byte between 5-255. This bytes is used as the key for the RXOR. Note, the unscram will not change when using the gen keyword (user-supplied key will cause the source to change when the supplied key changes).
- AES: Using srand() and rand() the 32-byte keys are randomly generated. The randomly generated key is written to the file MungePayloadAESKey.key. The key is XOR'd with a randomly generated byte between 5-255. Note, the unscram source does not change between Munges for AESAdvanced Encryption Standard encryption.
- Public\Private: Using SecureBuffer, the keys are randomly generated, the private key is then embedded in the header file. The key is XOR'd with a randomly generated byte between 5-255. Note, the unscram source does not change between Munges for Public\Private key encryption.
Design:
Examples:
Usage:
('section' missing)
No Obfuscation:
('section' missing)
XOR:
('section' missing)
XOR Randomly Generated Key:
('section' missing)
RXOR:
('section' missing)
Compression:
('section' missing)
AES:
('section' missing)
RSA (Pub/Priv):
('section' missing)
Combo - Compress, XOR, AES:
('section' missing)
Combo - All (just for fun):
('section' missing)
Stash Repository: Munge Payload Repository
Change Log:
('excerpt' missing)
SECRET//NOFORN