Vault7: CIA Hacking Tools Revealed

Navigation: » Latest version
Owner: User #14587667
Perseus 1.1.0b1 Test Notes
Perseus 1.1.0 Beta 1
MikroTik RB493G
General Info
WAN (from TR-Core) 172.20.100.4/30
TR-CoreSwx: 172.20.100.5 Perseus: 172.20.100.6
TR-Core Switch Route: 192.168.88.0/27 -> 172.20.100.6 (This gives the Perseus LANLocal Area Network 30 host IPs)
4/3/2015
- Changed RB493G ether1 IP to 172.20.100.6/30.
- Changed RB493G ether2 IP to 192.168.88.1/24.
- Default IP: 192.168.88.1/24
- Figure out how to run ChimayRed and TinyShell (TshPatcher).
4/8/2015
- Unable to connect RB493G to Console server. Checked MK website and confirmed settings, but no luck.
- Downloaded and upgraded MK f/w to v6.27
- Move Windows VMVirtual Machine to VLAN-602 (Perseus Internal).
- Use Winbox to upload new f/w. Copy "routeros-mipsbe-6.27.npk" using the Files List window.
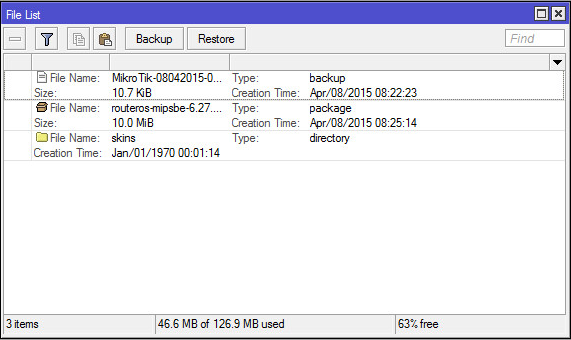
- Select System -> Reboot. Once rebooted, the new version number (6.27) will be seen in the Winbox Title.
4/9/2015
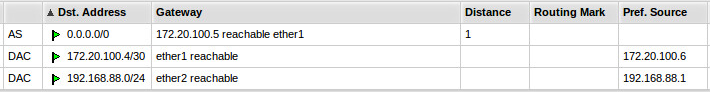
- Setup TR-Core route to 192.168.88.0/27
ip route 192.168.88.0 255.255.255.224 172.20.100.6 name Perseus-MK_RB493G
- MK routes
| ID | Status | Task |
|---|---|---|
| 1 | incomplete | Setup ACLAccess Control List (on TR-Core) to restrict VLANVirtual Local Area Network access |
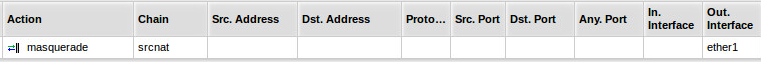
- Configure NATNetwork Address Translation on RS493G using the following rule:
Areas to test
stapmer.py
def parse_args(self, args):
# XXX TODO Bounds checks
# XXX Add checking for os version file, mcc, hide_files