Vault7: CIA Hacking Tools Revealed

Navigation: » Latest version
Owner: User #2064619
Cuckoo Sandbox
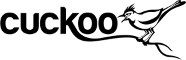
Overview
Cuckoo is an open source automated malware analysis system.
It’s used to automatically run and analyze files and collect comprehensive analysis results that outline what the malware does while running inside an isolated Windows operating system.
It can retrieve the following type of results:
- Traces of win32 APIApplication Programming Interface calls performed by all processes spawned by the malware.
- Files being created, deleted and downloaded by the malware during its execution.
- Memory dumps of the malware processes.
- Network traffic trace in PCAPPacket capture format format.
- Screenshots of Windows desktop taken during the execution of the malware.
- Full memory dumps of the machines.
For answers to general questions see: cuckoo.pdf
Instance
An in-work instance is at http://10.3.2.118:8080/. The instance has a 32-bit Windows XPWindows operating system (Version) SP3 sandbox and a 32-bit Windows 7 SP1 sandbox. Both sandboxes are limited to "host-only" networking and will not be able to resolve external network resources on DEVLAN (see TODO).